The article was written by Stas Yakobov,
Head of Research & IoT at Madsec security
תוכן עניינים
ToggleIntroduction
In the rapidly evolving landscape of Internet of Things (IoT) devices, cybersecurity is an emerging and critical concern. As these devices increasingly interweave with our daily lives, they become attractive targets for cyber threats. A vital aspect of IoT cybersecurity is understanding and analyzing the firmware governing these devices. This firmware is often stored in Serial Peripheral Interface (SPI) flash memory, making knowledge of SPI flash dumping crucial for IoT cybersecurity researchers.
This article will introduce the concept of SPI flash dumping using an affordable and accessible tool: the STM32 Blue-Pill Development Board. We will explore the role of flash storage in IoT devices, provide an overview of the STM32 Blue-Pill Dev Board, and explain how SPI flash can be dumped using this board. This discussion will help you appreciate the significance of SPI flash dumping in IoT cybersecurity. Whether you’re a seasoned cybersecurity professional or a novice in the field, you will gain valuable insights into the world of IoT cybersecurity from this piece.
Understanding IoT and Cybersecurity
The Internet of Things (IoT) has revolutionized the way we interact with the world around us. From smart homes and wearables to industrial sensors and smart cities, IoT devices are everywhere. They collect and share data, automate processes, and make our lives more convenient. However, with the proliferation of these devices comes a new set of challenges in the realm of cybersecurity.
IoT cybersecurity refers to the measures taken to protect IoT devices and networks against cyber threats. Given the vast amount of sensitive data these devices collect and transmit, they are attractive targets for cybercriminals. A breach could lead to unauthorized access, data theft, or even remote control over the devices.
The cybersecurity challenges in IoT are unique and complex. Unlike traditional IT devices, IoT devices often have limited computational power and memory, making it difficult to implement robust security measures. Furthermore, they are typically designed to be accessible and user-friendly, which can sometimes come at the expense of security.
Another challenge is the sheer number and diversity of IoT devices. With billions of devices connected to the internet, each with its own specific functionality and architecture, ensuring the security of each device is a daunting task.
Despite these challenges, IoT cybersecurity is not an insurmountable problem. It requires a thorough understanding of the IoT ecosystem, the potential risks involved, and the appropriate countermeasures. One such countermeasure is the ability to access and analyze the data stored on these devices, a process known as SPI flash dumping, which we will discuss in detail later in this article.
The Role of Flash Storage in IoT Devices
In the world of IoT devices, data storage is a critical component. While many microcontrollers used in IoT devices have built-in internal storage, it’s often not enough to handle the demands of complex IoT applications. This is where external flash storage, such as Serial Peripheral Interface (SPI) flash memory, comes into play.
External flash storage provides additional space where the device can store and retrieve data quickly and efficiently. This data can include the device’s operating system, applications, and user data. The use of external flash storage allows for greater storage capacity, flexibility, and in some cases, better performance.
SPI flash memory, in particular, is a popular choice for IoT devices due to its low cost, small size, and ease of integration. It uses a serial interface to communicate with the host device, allowing it to operate with fewer pins and take up less space on the device’s circuit board. This makes it an ideal choice for small, compact IoT devices.
The data stored in SPI flash memory typically includes the device’s firmware. Firmware is a type of software that provides low-level control for the device’s specific hardware. It serves as the device’s operating system, instructing the device on how to carry out its functions.
In the context of IoT cybersecurity, the firmware stored in SPI flash memory can provide valuable insights. By analyzing the firmware, security researchers can understand how the device operates, identify potential vulnerabilities, and develop strategies to mitigate these risks. One common method for analyzing firmware is through a process known as SPI flash dumping, which involves reading the data stored in the SPI flash memory.
STM32 Blue-Pill Dev Board: An Affordable Solution
In the field of IoT cybersecurity, having the right tools is crucial. One such tool that has gained popularity among researchers and hobbyists alike is the STM32 Blue-Pill Development Board. This small yet powerful board offers a range of features that make it an excellent choice for tasks such as SPI flash dumping.
The STM32 Blue-Pill Dev Board is powered by the STM32F103C8T6 microcontroller, a 32-bit ARM Cortex M3 chip. It operates at a frequency of 72 MHz and offers a range of peripherals, such as SPI, I2C, and USART interfaces. This makes it versatile and suitable for a variety of tasks.
One of the key advantages of the STM32 Blue-Pill Dev Board is its affordability. Unlike many other development boards, the STM32 Blue-Pill Dev Board is competitively priced
Dumping SPI Flash Using STM32 Blue-Pill Dev Board
Preparation
Collect the essential tools and equipment before diving into the SPI flash dumping process. The toolkit includes the STM32 Blue-Pill Dev Board, a Linux-based computer (preferably Kali Linux due to its pre-installed necessary tools and libraries), a micro USB cable, a USB to UART bridge, Dupont cables, and the SPI flash memory-containing IoT device.
Installing The Firmware
Equip the STM32 Blue-Pill Dev Board with specific firmware to enable it to function as a flashrom serprog programmer. This firmware is available at this GitHub repository. Once the firmware is successfully installed, you’re ready to connect the board to the SPI flash.
Dumping the SPI Flash
Start by familiarizing yourself with the Serial Peripheral Interface (SPI) protocol, a popular standard for synchronous serial data communication in embedded systems. Our STM32 Blue-Pill Dev Board, the master device, needs to communicate with the SPI flash memory, the slave device. They connect via various lines such as MOSI, MISO, SCK, CS, VCC, and GND. Establishing these connections correctly is the cornerstone of the SPI flash dumping process.
In this section, we will be using the flashrom tool to detect and dump the SPI flash chip for the following example the chip we are using is “Winbond W25Q64JV” . flashrom is a universal flash programming utility that can be used to detect, read, write, verify, and erase flash chips. It supports a wide range of DIP32, PLCC32, DIP8, SO8/SOIC8, TSOP32, and TSOP40 chips, which use various protocols such as LPC, FWH, parallel flash, or SPI.
The first step is to detect the SPI flash chip. This can be done using the following command:
flashrom -p serprog:dev=/dev/ttyACM1,spispeed=1M
If we properly wired our STM32 Blue-Pill to the SPI flash, we should get output similar to this:
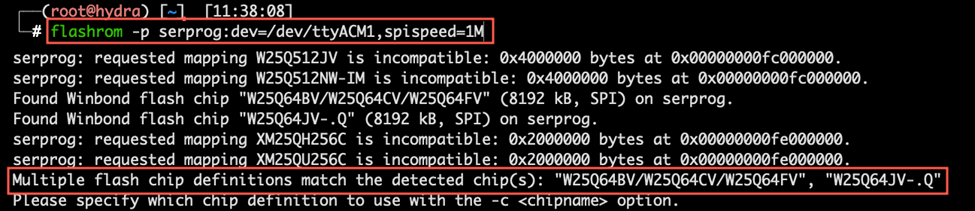
As you can see, the tool has detected a Winbond flash chip “W25Q64JV-.Q”. Once the connection and chip detection are confirmed, you’re ready to read the SPI flash memory’s content. Flashrom comes into play again, reading the data and saving it to a file, generally in binary format. This file contains the IoT device’s firmware.
Next, we will dump the content of the flash using the suggested chip name:
flashrom -p serprog:dev=/dev/ttyACM1,spispeed=1M -c W25Q64JV-.Q -r firmware.bin
Flashrom will try to read the content of the SPI flash and save it to firmware.bin
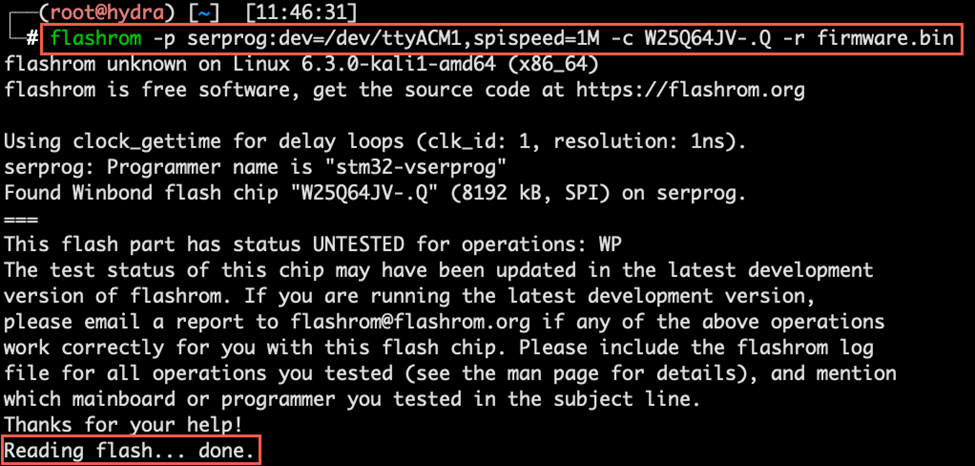
As we conclude the dumping process, our next step is to delve into the analysis of the saved output file, unlocking the potential insights it holds.
Analyzing the Dumped Data
The analysis of dumped data from SPI flash memory is a journey that extends beyond the confines of a single IoT device. The data, whether it’s full or partial firmware or operational data, serves as a window into the broader ecosystem in which the device operates.
Now that we have dumped the firmware, we can analyze it using binwalk. binwalk is a tool for searching binary images for embedded files and executable code. It is particularly useful for analyzing firmware images.
To extract the content of the dumped firmware, we can use the following command:
binwalk –run-as=root -e firmware.bin
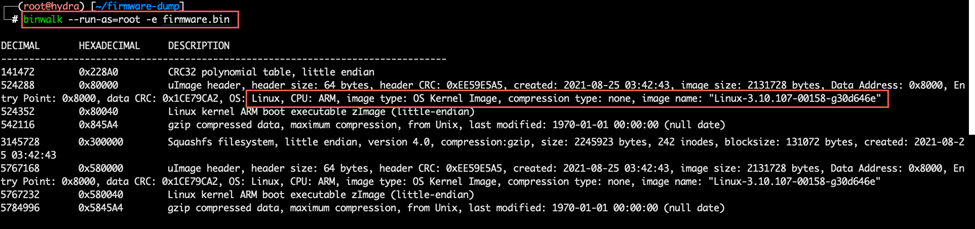
As you can see, the output shows that the firmware is based on ARM Linux.
Inspecting the extracted content of the firmware exposes private RSA key in the .ssh folder:
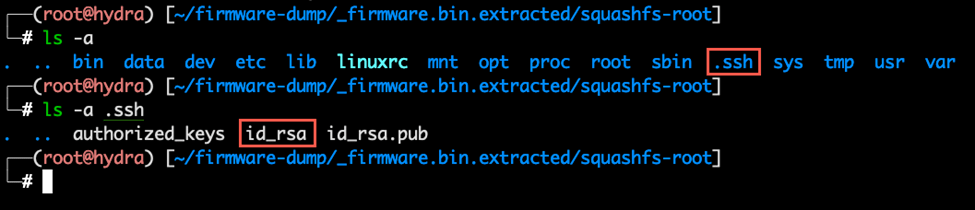
Discovering a private RSA key in the .ssh folder opens up a range of possibilities. For instance, it could provide a gateway to the IoT system’s backend server. This key can be a powerful tool, enabling us to explore further within the IoT ecosystem of the device, potentially facilitating lateral movement and deeper access.
Analyzing Stored Data: Risks, Insights, and Security Measures
The analysis of data stored in memory, such as SPI flash, can reveal a wealth of information about the device and its broader ecosystem. This data can include sensitive information like encryption keys, certificates, or passwords. If not properly secured, these could be exploited by attackers to gain unauthorized access to the system. Identifying such sensitive data is a crucial step in securing IoT devices and their associated systems.
The stored data can also shed light on the device’s communication endpoints, which could range from server addresses and API endpoints to other IoT devices within the network. Understanding these connections is vital for identifying potential vulnerabilities and securing the entire system.
In addition, the data can provide insights into the device’s role and capabilities within the larger system, revealing its responsibilities, the nature of the data it handles, and the operations it performs. This understanding can help identify potential attack vectors and areas that require bolstered security measures.
The firmware stored in memory could potentially contain backdoors or other exploitable bugs. These hidden gateways could be used by attackers to gain control over the device or even access the larger system it operates within.
Lastly, the security measures implemented by the device can be assessed through the analysis of the dumped data. This includes the evaluation of data encryption standards, the methods employed for credential storage, and the security of communication protocols. Identifying and addressing inadequate security measures is essential to prevent unauthorized access and data breaches.
Conclusion
In our increasingly interconnected world, Internet of Things (IoT) devices have become an integral part of our daily lives and business operations. As these devices continue to proliferate, understanding and securing them is not just a necessity, but a critical responsibility. This article has shed light on the importance of firmware analysis in IoT devices, a key step in identifying and mitigating potential security risks.
We’ve explored the technique of SPI flash dumping, a valuable method that provides insights into the operation and potential vulnerabilities of IoT devices. By using affordable and accessible tools like the STM32 Blue-Pill Development Board, this process is achievable even with budget constraints, making cybersecurity more accessible to all.
Moreover, we’ve emphasized the need for organizations to incorporate IoT security into their broader cybersecurity strategy. As IoT devices become more deeply embedded in business operations, they become increasingly attractive targets for cybercriminals. Implementing robust security measures, including regular security audits, is essential to detect and rectify vulnerabilities before they can be exploited.
As we navigate this new era in cybersecurity, the focus is shifting towards securing the rapidly expanding IoT landscape. This is a collective responsibility, requiring the efforts of developers, manufacturers, researchers, and users alike to bolster IoT security and contribute to a safer digital world.
Arming ourselves and our organizations with the right knowledge and tools to analyze and secure IoT devices is a crucial step in this cybersecurity journey. As the importance of IoT cybersecurity continues to grow, it opens up new opportunities for professional services specializing in this field to help navigate these complexities. After all, our collective security depends on our collective effort.
For those interested in diving deeper into IoT cybersecurity, there are numerous resources available. From comprehensive overviews of the Serial Peripheral Interface (SPI) to specific firmware required by the STM32 Blue-Pill Dev Board, the knowledge is out there, waiting to be tapped into. The journey into IoT cybersecurity is a continuous one, filled with constant learning and adaptation. As we continue to innovate and evolve, so too must our approach to securing our digital world.
References
- SPI Overview by SparkFun A comprehensive overview of the Serial Peripheral Interface (SPI), which is widely used in IoT devices for fast data transfer.
- Flashromis a universal flash programming utility that allows you to read, write, erase, and verify BIOS/ROM/flash chips.
- BinwalkBinwalk is a fast, easy to use tool for analyzing, reverse engineering, and extracting firmware images###
- STM32-vserprog GitHub Repository This repository contains the specific firmware required by the STM32 Blue-Pill Dev Board to function as a flashrom serprog programmer.
- STM32F103C8T6 Blue Pill Board Information detailed overview of the STM32F103C8T6 Blue Pill Board, its specifications, and other relevant information.

